An enterprise vulnerability management program can reach its full potential when it is built on well-established foundational goals that address the information needs of all stakeholders, its output is tied back to the goals of the enterprise, and there is a reduction in the overall risk of the organization. A vulnerability can be defined as a defect or bug that allows an external entity to directly or indirectly influence the availability, reliability, confidentiality or integrity of a system, application, or data. New vulnerabilities appear daily because of software flaws, faulty configuration of applications, and human error.
This paper is from the SANS Institute Reading Room site. Reposting is not permitted without express written permission.
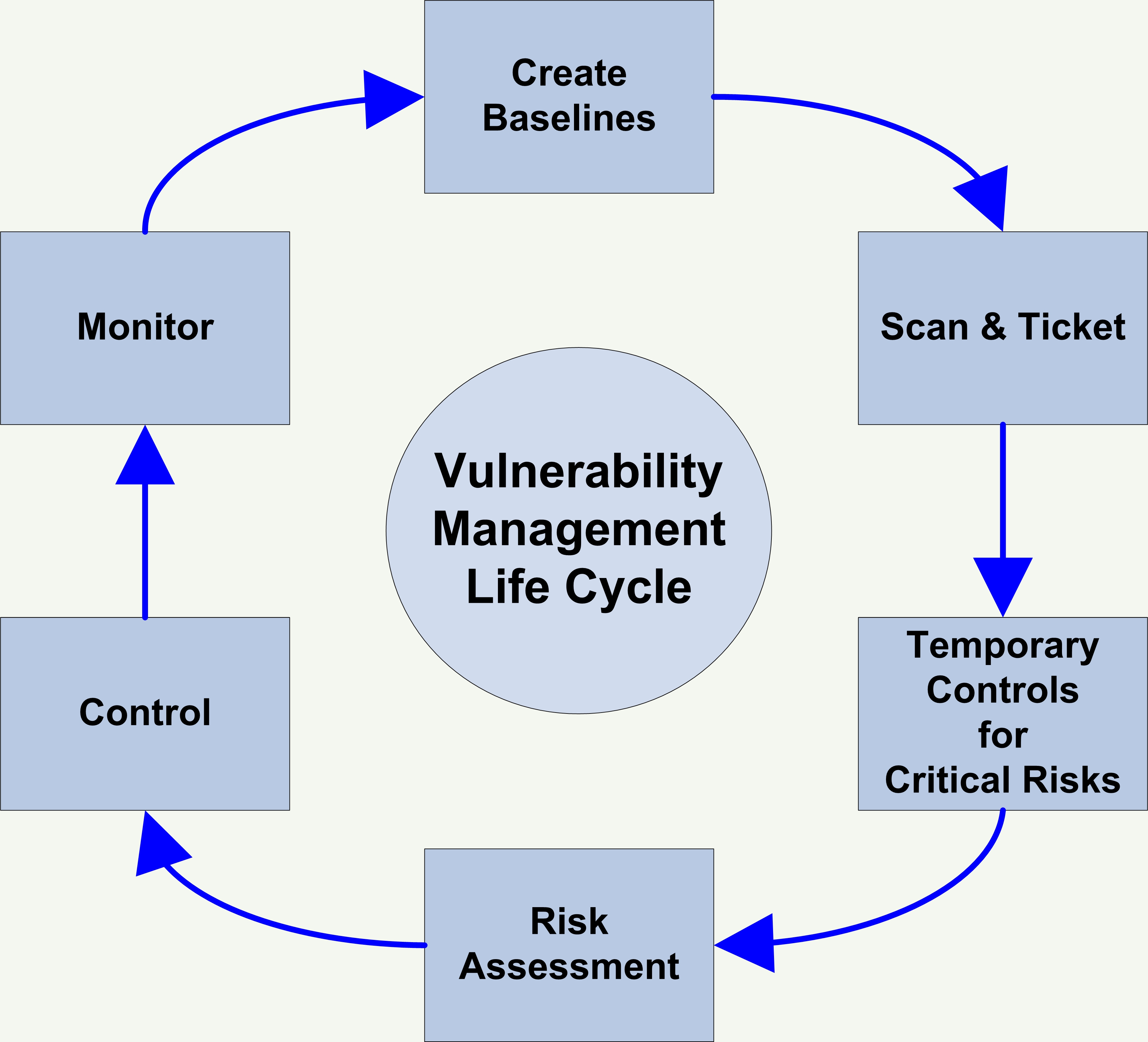
Vulnerability Management : Tools, Challenges and. Here are four best practices to re-invent your vulnerability management process. One quick security benefit of knowing what your assets are running is knowing when new vulnerabilities come out and what assets they affect without running a scan. Sometimes the best practice you can implement in your vulnerability management program is not having . This checklist of best practices will save you time and help you . How often is vulnerability data collected? How much of the network is covered?
Is scanning disruptive to the business?

Are you able to find alternatives to patching ? Do you prioritise by possible business impact? Is risk level increasing or decreasing over time? All information presented here is subject to change and intended for general information.
An EiQ Networks White Paper. When building the concepts for a new framework for vulnerability management and assessment, I have devised a few known- good techniques. The first is to throw out continuous scanning and point-in time assessments. The concept of vulnerability management and assessment is normalized with other . Resources must be allocated to put a program in place that can deal with a multitude of attacks. In this tip, we will offer five best practices that companies can implement to increase the effectiveness of their threat and vulnerability management program.
To break the high-priority habit, here are the top four best practices you should adopt to ensure you have a comprehensive vulnerability management program in place that will help you successfully navigate the increasingly dense, diverse and dangerous world of cybersecurity threats. Inventory all assets connected to your network, you . Watch this webinar to discover best practices and ROI of the most successful business risk-centric vulnerability management programs. Good planning is essential for.
Assign owners to your. Students develop the capability to assess and analyze on-premise and cloud system vulnerabilities. Students conduct controlled exploitation and produce an effective remediation plan through the in-depth application of the Common Body of Knowledge (CBK) for the Certified Ethical Hacker v (CEHv9) certification.

I addressed this practice in the “Cloud Security Best Practices ” blog post. This post expands on the practice of vulnerability scanning and management for the IT security team tasked with the responsibility of dealing with an external cloud .